Perimeter 81 fast factsOur rating: 3.9 out of 5 stars
|
Perimeter 81 is a cloud-based network security solution designed to help organizations boost security on corporate networks. The solution takes network security beyond the capabilities of traditional VPNs and firewalls, with over 50 points of presence worldwide and a range of security features. These features include a zero-trust architecture, advanced malware protection, and device posture check.
Continue reading to learn more about Perimeter 81 and what it offers as a network security solution.
Semperis
Employees per Company Size
Micro (0-49), Small (50-249), Medium (250-999), Large (1,000-4,999), Enterprise (5,000+)
Large (1,000-4,999 Employees), Enterprise (5,000+ Employees)
Large, Enterprise
Features
Advanced Attacks Detection, Advanced Automation, Anywhere Recovery, and more
ESET PROTECT Advanced
Employees per Company Size
Micro (0-49), Small (50-249), Medium (250-999), Large (1,000-4,999), Enterprise (5,000+)
Any Company Size
Any Company Size
Features
Advanced Threat Defense, Full Disk Encryption , Modern Endpoint Protection, and more
ManageEngine Log360
Employees per Company Size
Micro (0-49), Small (50-249), Medium (250-999), Large (1,000-4,999), Enterprise (5,000+)
Micro (0-49 Employees), Small (50-249 Employees), Medium (250-999 Employees), Large (1,000-4,999 Employees), Enterprise (5,000+ Employees)
Micro, Small, Medium, Large, Enterprise
Features
Activity Monitoring, Blacklisting, Dashboard, and more
Perimeter 81 pricing
Perimeter 81 offers four paid plans: Essentials, Premium, Premium Plus, and Enterprise.
Here’s a brief overview of their feature and price differences:
| Plans | Essentials | Premium | Premium Plus | Enterprise |
|---|---|---|---|---|
| Price | $8 per user per month. | $12 per user per month. | $16 per user per month. | Quote available upon request. |
| Users | Minimum 10 users. | Minimum 10 users. | Minimum 20 users. | Minimum 50 users. |
| Unlimited network tunnels | Yes | Yes | Yes | Yes |
| Split tunneling | Yes | Yes | Yes | Yes |
| Single Sign-On capabilities | No | Yes | Yes | Yes |
| Logs retention | 14 days. | 30 days. | 30 days. | 60 days. |
| Dedicated chat and email support | During office hours only. | Prioritized response. | Prioritized response. | 24/7 |
The Perimeter 81 pricing structure is similar to some of its competitors, like NordLayer. For example, the annual billing in the Premium and Premium Plus cost $12/user/month and $16/user/ month respectively. Meanwhile, their equivalents in NordLayer — Core and Premium — cost $11 per user/month and $14 per user/month, respectively.
Perimeter 81 is costlier when you place it side by side with Twingate, whose highest pricing is $10 per user/month for annual billing.
While there is no free trial available, I commend Perimeter 81 for offering a 30-day money-back guarantee for each of their plans. I also appreciate how prospective buyers can request a demo to join a call and receive a 15-minute walkthrough of the VPN.
SEE: Free VPN vs Paid VPN: Which One Is Right for You? (TechRepublic)
Is Perimeter 81 safe?
Yes, I found Perimeter 81 to be a safe and secure VPN software solution. Perimeter 81 has a lot of advanced security features that make it a safe VPN for different organizations. The tool features multi-factor authentication (MFA), prompting employees to pass through a multi-step account login process before gaining access to a company’s resources.
As an enterprise solution, I appreciate that Perimeter 81 offers single sign-on, which integrates with business services like Azure, Google Suite, LDAP, or OKTA to streamline safe login for company employees working remotely. However, I want to mention that SSO isn’t available on the Essentials plan — so keep that in mind when considering their subscriptions.
The solution also employs AES-256 encryption using IPsec or WireGuard protocols and supports network security features such as split tunneling, web filtering, a firewall, and an Always On VPN option. Another notable security feature is Automatic Wi-Fi protection, which ensures that employees don’t get access to company resources when their connection is exposed.
SEE: 10 Ways a Zero Trust Architecture Protects Against Ransomware (TechRepublic)
One major safety concern I have about Perimeter 81 is its logs policy. The provider keeps IP log data for up to 60 days before it is deleted. However, Perimeter 81 claims only the workspace admin has access to that data.
Key features of Perimeter 81
Below are some features of Perimeter 81 I found interesting.
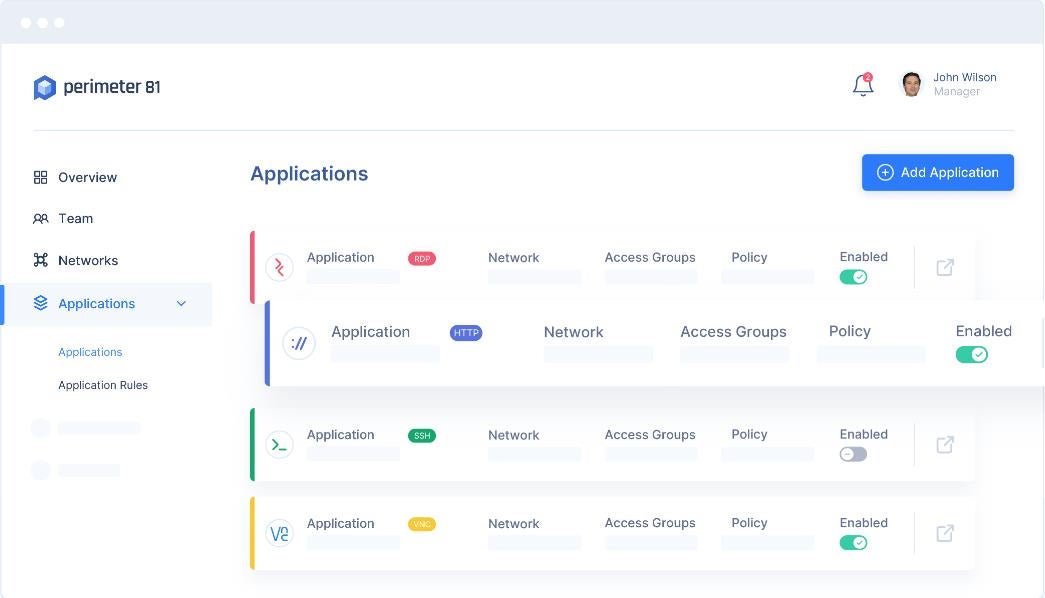
Agentless application access
One of my favorite Perimeter 81 features is its Agentless Zero Trust Network Access. It works by giving employees or third-party contractors limited access to a company network. The feature can grant specific employees access through the browser to a particular application — not the wider company network. This helps admins monitor employee or third-party contractor access to company networks to know where and how access occurs.
SEE: How to Create an Effective Cybersecurity Awareness Program (TechRepublic Premium)
DNS Filtering
Another Perimeter 81 inclusion I like is its DNS Filtering. This feature limits users’ access to unauthorized websites that could harm a company’s network infrastructure. It helps IT teams determine which content or IP address will be whitelisted or blacklisted on employees’ devices.

I envision this to be especially beneficial for hybrid workforces and businesses with fully remote workers.
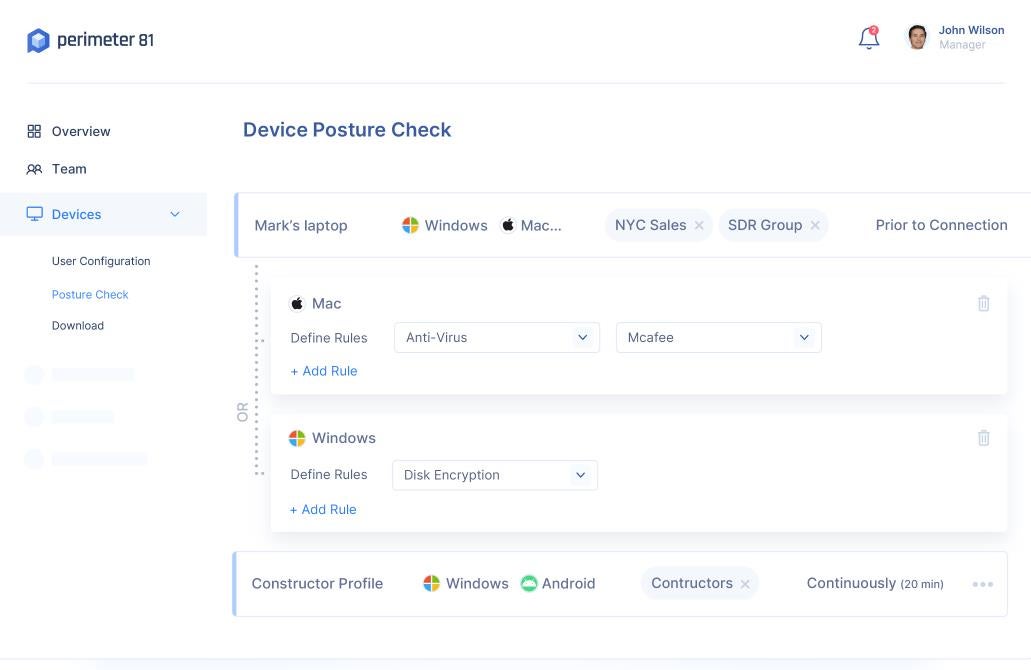
Device Posture Check
If your department regularly handles sensitive data, I suggest looking into Perimeter 81’s Device Posture Check or DPC. DPC ensures the company’s most important resources are secured by granting access strictly to only devices that meet the security posture requirements. Perimeter 81 DPC rules can check Android, iOS, Windows, MacOS, and Linux devices before and during network access, and remove devices where there is a discrepancy between user policy and posture.
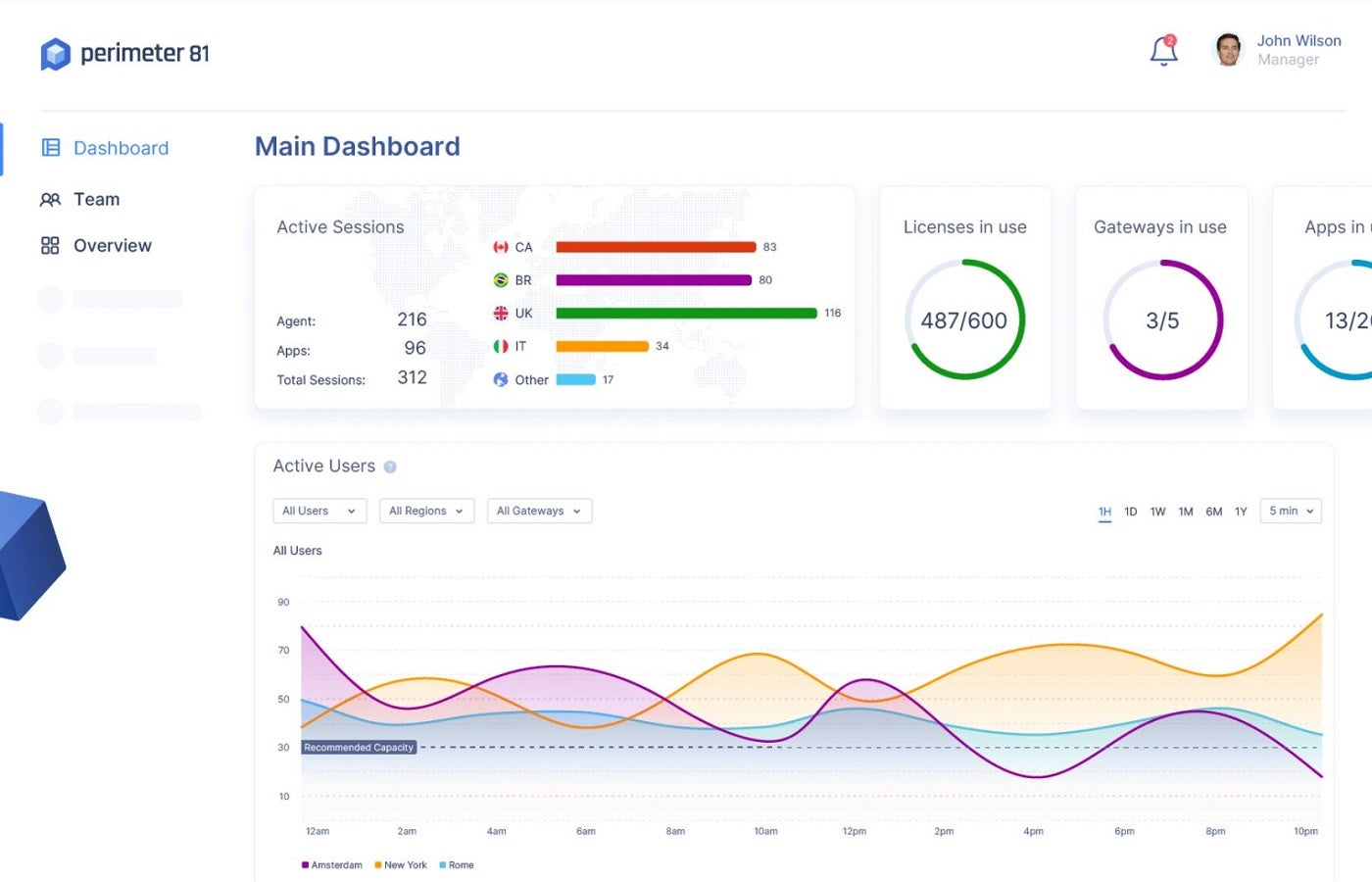
Advanced Malware Protection
For more traditional threat protection, Perimeter 81’s Advanced Malware Protection is a welcome feature. It uses a combination of signature-based detection, heuristics, and advanced machine learning to identify and block malware and zero-day attacks. Personally, I appreciate how it enables admins to easily track user exposure to malicious content with extensive reports.
SEE: How to Tell If Your VPN Is Working Properly (TechRepublic)
What operating systems, ID providers, and cloud services is Perimeter 81 compatible with?
Per my research, Perimeter 81 supports all the major operating systems and devices. Specifically, it supports the following:
- Windows 10 or later.
- macOS 11 or later.
- Linux 7 or later.
- iOS 15 or later.
- Android 8.1 or later.
When it comes to popular enterprise applications and cloud services, Perimeter One is compatible with Amazon AWS, Google Cloud, and Microsoft Azure. For identity providers and SAML 2.0 providers, I applaud Perimeter 81 for having broad support overall. Right now, it’s compatible with:
- Google.
- Auth0.
- Azure AD.
- ADFS.
- Rippling.
- Okta.
- OneLogin.
- JumpCloud.
- PingIdentity.
- PingFederate.
As a disclaimer, the above list reflects IdPs supported as of October 2024.
Perimeter 81 pros
- User interface is easy to understand.
- Integrates with many third-party solutions like Azure, Google Suite, LDAP, and OKTA.
- 50+ global data centers.
- Offers unsegmented network access.
- Supports multiple platforms and operating systems.
- Offers a 30-day money-back guarantee.
Perimeter 81 cons
- Free trial and free version not available.
- Vital security features not included in some plans.
- Keeps IP logs for up to 60 days depending on plan.
Who is Perimeter 81 for?
I recommend Perimeter 81 for medium to large organizations with employees who require secure remote access to their company’s internal network. From my review, Perimeter 81 might not be suitable for smaller businesses unless you’re willing to pay for the higher plans to have access to its full security features.
Perimeter 81 alternatives
While Perimeter 81 can be a good security solution for most organizations, there are still other noteworthy alternatives to check out if you feel Perimeter 81 doesn’t fit your needs. Below are two I’ve analyzed and consider as good substitutes.
NordLayer

NordLayer is a secure remote access solution from Nord Security. NordLayer’s paid plan enables you to create secure connections between remote devices and corporate networks. One added advantage NordLayer has over Perimeter 81 is the 24/7 live/email support provided across all its plans. Perimeter 81 offers live support on higher plans only.
Twingate

If you’re a small team or an individual on a budget and looking for a good network security alternative to Perimeter 81 that offers a free plan, Twingate might be a good pick. The tool is a cloud-based service that provides secure remote access to an organization’s networks. Pricing starts at $5/user/month for annual billing. This is much cheaper than Perimeter 81, which starts at $8 per month. Additionally, the tool offers a 14-day free trial across all its premium plans.
SEE: Different Types of VPNs & When to Use Them (TechRepublic)
Review methodology
My review of Perimeter 81 is based primarily on the user experience, integration capabilities, and security features. Most of my analysis was done by collecting information from the Perimeter 81 website, where I reviewed and compared their capabilities with other similar services like NordLayer and Twingate. I also looked into user feedback on the product from popular review sites to gain insights into what users are saying about the solution.
I rated Perimeter 81 using an internal algorithm to get a rating of 3.9 out of 5 stars. The scoring was based on Perimeter 81 on its own and in relation to other VPNs available today.
Read the full article here














