Apple’s approach to building new features has always been rooted in safety and seamless convenience. Take, for example, AirPlay, a wireless standard created by the company that allows users to stream audio and video from one device to another.
AirPlay works not just across Apple devices, but also on TVs and speakers cleared by the company to offer the wireless streaming facility. That also makes it a ripe target for attacks, and it seems there are, in fact, vulnerabilities in the wireless lanes that could allow bad actors to seed malware and infect more connected devices.
Understanding the AirPlay risk
Experts at the security research firm Oligo recently detailed Airborne, a set of flaws in Apple’s AirPlay Protocol and the AirPlay Software Development Kit (SDK) that can allow hackers to remotely execute code. These vulnerabilities can let bad actors take control of devices and use the infected machines to broaden the damage.
“An attacker can take over certain AirPlay-enabled devices and do things like deploy malware that spreads to devices on any local network the infected device connects,” Oligo explained. The risk is huge because there are billions of Apple devices out there that support AirPlay, and millions that are sold by other brands.
One of the vulnerabilities could allow hackers to compromise a device and then use it to gain access to a larger network, potentially targeting other devices, too. Depending on the target, the risks range from spying on conversations to tracking a car’s location, accessing sensitive information, ransomware attacks, and denial of service.
Apple has patched the vulnerabilities via macOS Sequoia 15.4, tvOS 18.4, macOS Ventura 13.7.5, iPadOS 17.7.6, macOS Sonoma 14.7.5, iOS 18.4 and iPadOS 18.4, visionOS 2.4 updates. However, there are potentially thousands of older devices that will never get patched and remain vulnerable.
What steps do experts suggest?
Of course, the first line of defense to protect yourself across all vulnerable devices is to download the fix released by Apple. But that isn’t the full picture. Trevor Horwitz, CISO and founder of TrustNet, says the patch will only work if people install it after the package downloads on their device.
“The simplest and most effective thing you can do is keep your devices updated. That sounds basic, but it’s often overlooked,” he says. On an iPhone or iPad, follow this route to install the safety update: Settings > General > Software Update. For macOS, you must walk this path: Apple menu > System. Settings > General > Software Update.
Since attack vectors like Airborne rely on Wi-Fi networks to expand their damage, you must also pay attention to them. Oleh Kulchytskyi, Senior Malware Reverse Engineer at MacPaw’s Moonlock, told DigitalTrends that a Zero-Click Remote Code Execution (RCE) is the highest level of security breach.
It should be immediately patched by the companies involved, but as a user, one must take further network-related precautions. “To stay safe at home, ensure that your router has a strong password and there are no suspicious connections to your network,” Kulchytsky adds.
A safe way to AirPlay
Matthias Frielingsdorf, a veteran iOS researcher and cofounder of iVerify, tells me that everyone should follow basic digital security protocols. Those include installing updates as soon as they are available, maintaining strong network passwords, and most importantly, reducing the surface area for such attacks.
Since AirPlay is the threat vector, users should take proactive steps while using it. ”Disabling this on iOS / macOS / tvOS devices that don’t need to be an AirPlay receiver would limit some of the attacks. In public spaces, disabling WiFi on the Mac and iPhone would stop those attacks as well,” says Frielingsdorf.
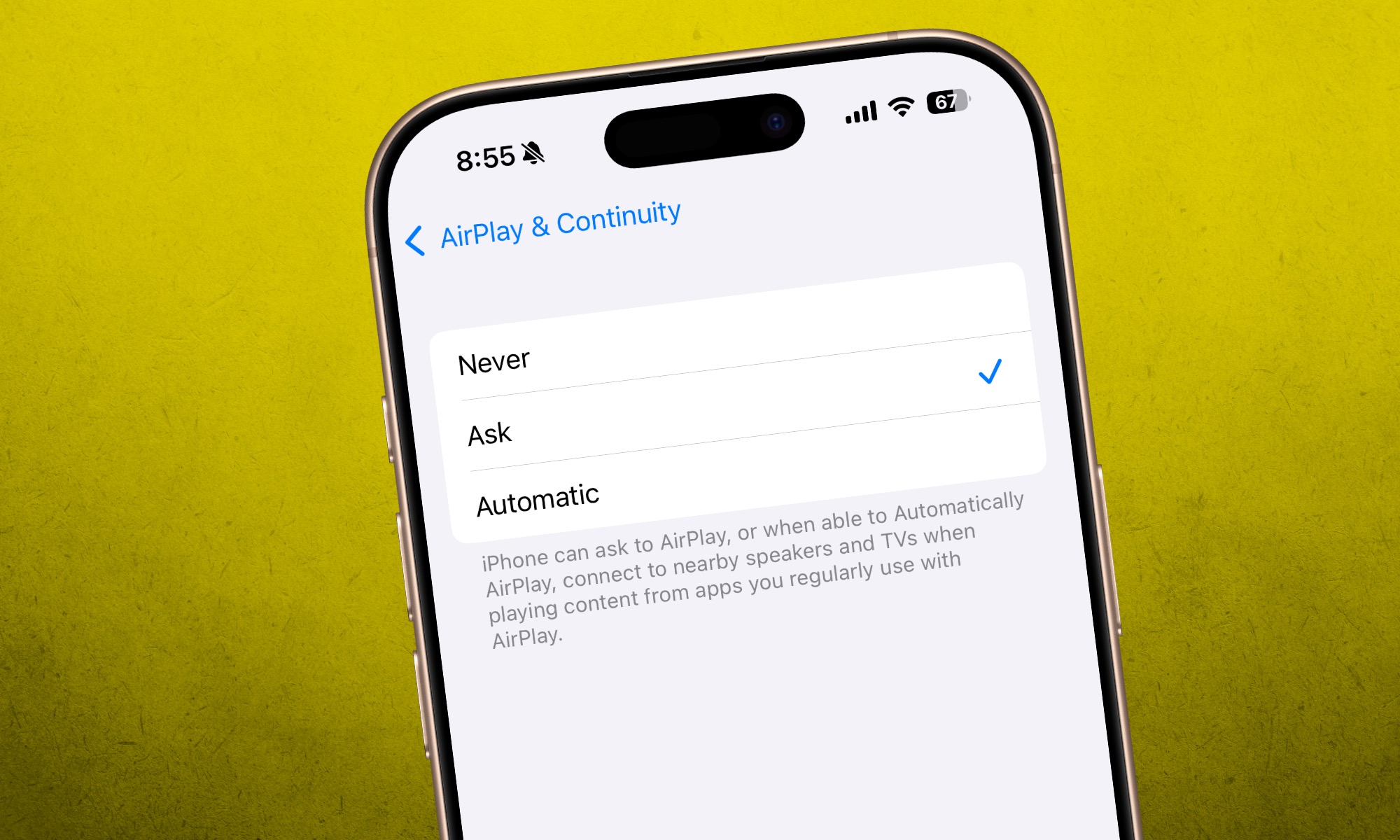
AirPlay streaming is active by default, and as such, you need to disable it. To do so, follow this path on your iPhone or iPad: Settings > General > AirPlay & Continuity > Ask. You can also set it to Never, if you don’t actively utilize this feature. There’s also an option to set a password, which I recommend that you enable, while at it.
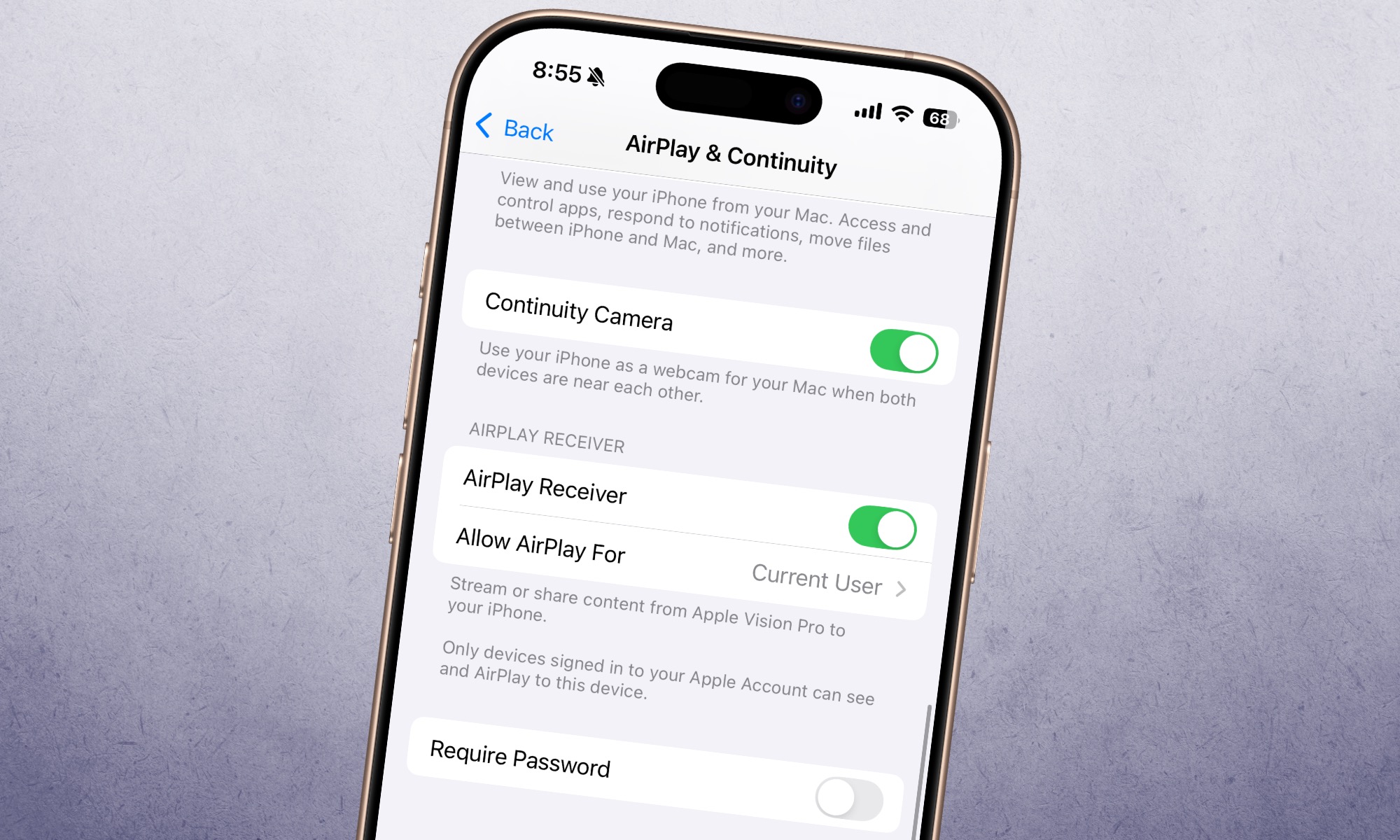
What about AirPlay itself? Can it be disabled? Yes, it can be turned off entirely. On your iPhone and iPad, go to the AirPlay & Continuity page and turn off the AirPlay Receiver toggle. Alternatively, you can choose to allow AirPlay only for the Current User, instead of keeping it open to everyone in the range.
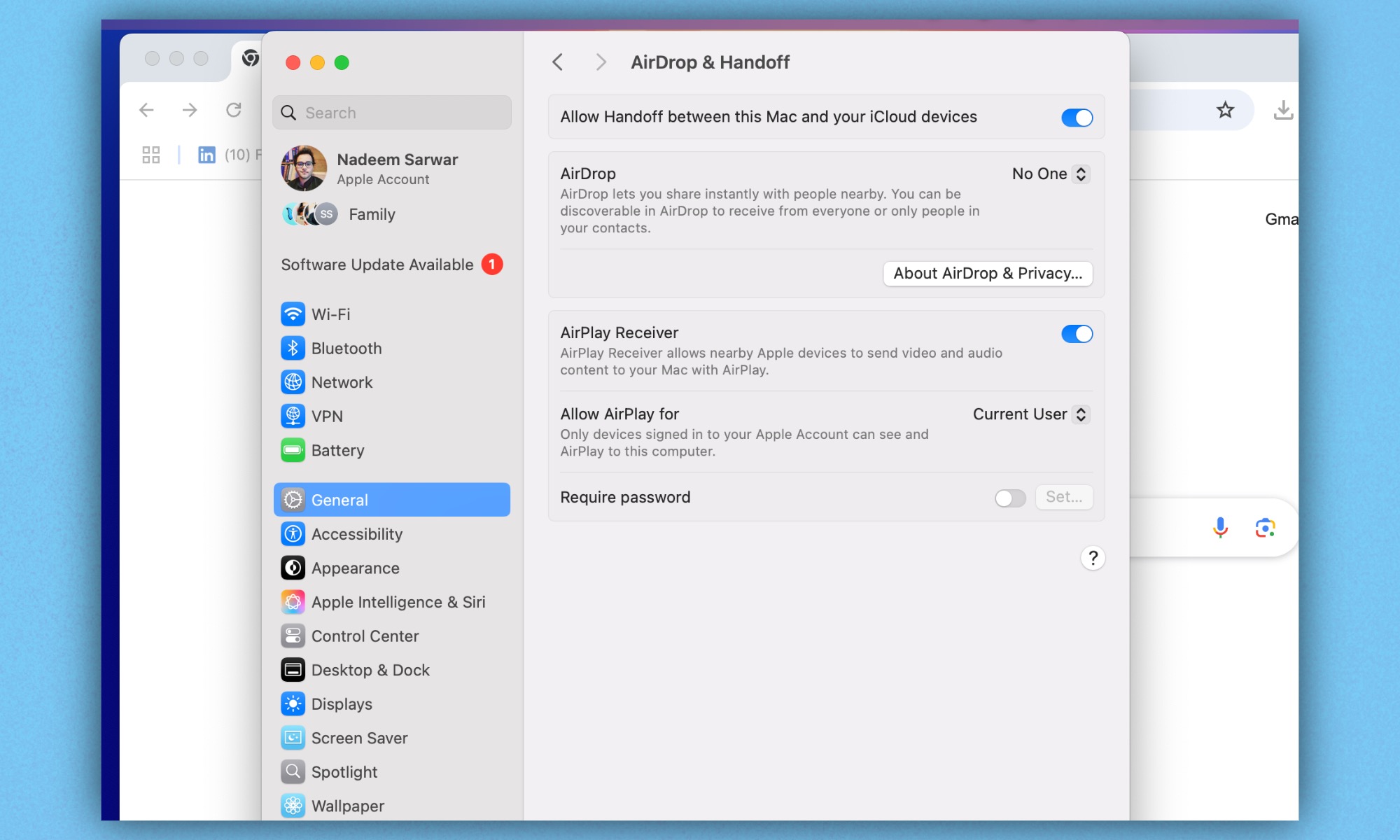
For Mac users, this is the path you need to follow: Apple Menu > System Settings > General > AirDrop & Handoff > AirPlay Receiver. You can’t always patch older or discontinued devices, so it’s best to ensure that the machines that are currently in your hands have enabled the right protocols to minimize the risks.
The bottom line
On multiple occasions in the past, security experts have highlighted flaws in wireless transmission systems, such as Bluetooth. But a vulnerability that allows zero-click remote code execution in AirPlay is a cautionary tale. The message is clear.
Apple’s security guardrails are solid, but not impenetrable.
“What makes this serious is the integration. AirPlay isn’t just a standalone app. It’s a system-level service built into iOS, macOS, and tvOS. So the moment that layer is compromised, the attacker could potentially affect multiple devices at once,” TrustNet’s Horwitz told Digital Trends.
So, where does that leave an average user who is not savvy about security measures? Well, it’s time to set aside notions and market perceptions. Chris Hill, Chief Security Strategist at BeyondTrust, says users must understand the threat landscape instead of living with the idea that a certain ecosystem is safer than the rest.
“Threat actors are opportunistic, looking for the easiest path of least resistance, they will find it, and they did in this case with AirPlay and AirBorne,” he warns. The bottom line is that keep your devices updated, disable features you don’t use, and be vigilant with network-related settings.
Read the full article here