This review first appeared in issue 360 of PC Pro.
WatchGuard’s Firebox M390 shows that high-end security appliances don’t always command a high price. Targeting busy SMBs with up to 250 users, this affordable 1U rack model boasts a top raw firewall throughput of 18Gbits/sec, dropping to a respectable 2.4Gbits/sec with all UTM security services enabled.
A simplified licensing scheme makes it easy to manage costs. We’ve shown the price of a Total Security Suite (TSS) subscription, which enables everything WatchGuard has to offer. This includes gateway antivirus, anti-spam, web content filtering, application controls, intrusion prevention services (IPS) and an advanced persistent threat (APT) blocker with cloud sandboxing.
You also get WatchGuard’s reputation enabled defense (RED) cloud-based URL filtering, ThreatSync XDR for collection, correlation and automated responses to threat events, and DNSWatch to monitor client DNS requests and block access to known malicious domains. It has enough power to run the Cylance AI-based IntelligentAV malware scanning engine; the elderly dual-core Celeron in the M370 has been upgraded to an 8-core NXP LS2084A CPU.
There’s room to grow, as the front expansion bay accepts modules with gigabit, 10GbE or 2.5GbE multi-gigabit ports. Note that the PoE+ services on the multi-gig module will be disabled as the M390 doesn’t support the required 54V power supply, which is only available on the M590 and M690 models.
The appliance is easy to deploy. Its web console wizard sorts out the LAN and WAN network interfaces and applies a base set of firewall policies that include blocking common undesirable web categories. We had already registered the appliance’s serial number with our cloud support account so the wizard grabbed our TSS feature key and applied it.
The M390 can be managed in standalone mode, but businesses with multiple appliances will prefer WatchGuard’s Cloud portal, which is included in both the Basic Security Suite (BSS) and TSS subscriptions. Two choices are available: you can keep local management and set the appliance to send its logs to the cloud for remote monitoring and reporting or move it all into the cloud.
Full cloud management is activated by allocating the appliance from your account inventory and enabling it from the local console. The portal steps through WAN port setup and applying new admin passwords, after which the appliance disables local management.
Cloud configuration is simple as the portal groups all security settings for the appliance in one page. From the content scanning section you activate antivirus scanning, APT blocking, IntelligentAV and anti-spam policies for incoming SMTP, IMAP or POP3 traffic.
The network blocking section covers botnet detection, IPS, port and site blocks and detection of Tor exit points. WatchGuard’s WebBlocker service is accessed in the content filtering section and offers 166 URL categories that can be allowed, blocked or set to display a warning page to users.
Each content filter action policy manages both web access and application controls. The latter presents nearly 1,300 predefined app and protocol signatures, with Facebook and X activities getting the lion’s share of the social networking category. They’re easy to apply; when creating firewalls rules, you simply choose the action policy you want to assign.
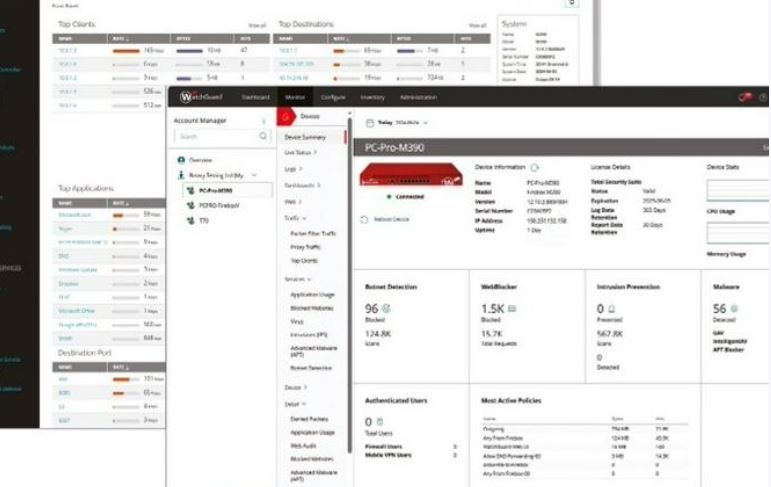
The portal’s monitoring page provides a wealth of information on all activities. Graphs and charts are provided for live activity, traffic, detected malware and botnets, application usage, blocked websites, top clients and much more.
The Firebox M390 will appeal to SMBs with a large user base. It combines strong performance with an incredible range of security measures all at a competitive price. It’s easy to deploy and WatchGuard’s cloud portal delivers excellent remote management and monitoring features.
We also rated the best anti-virus software for PC.
Read the full article here